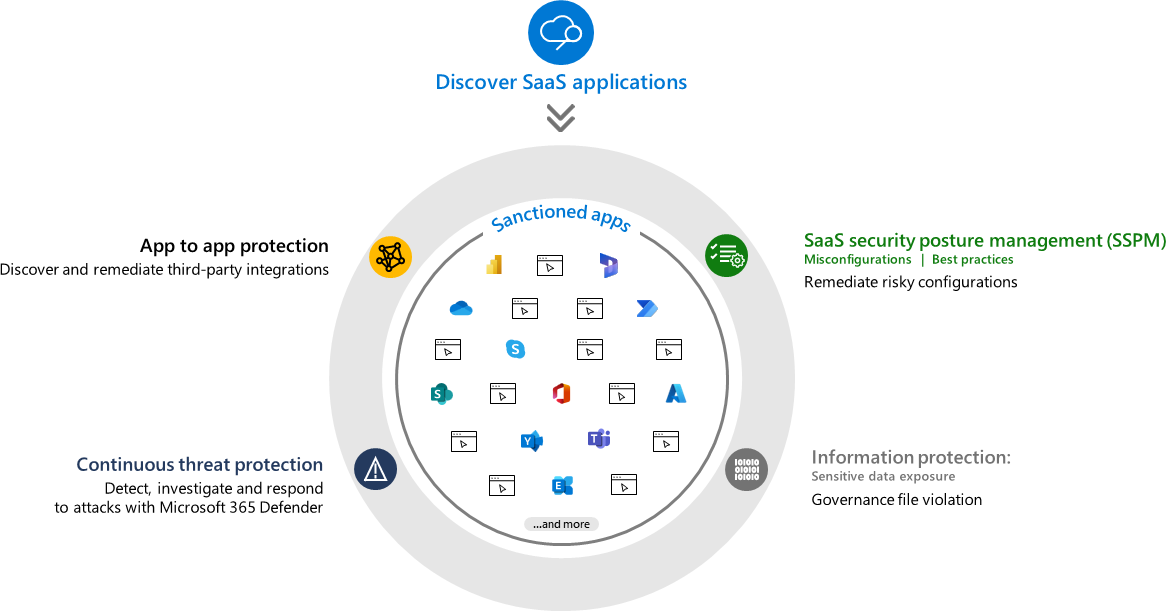
What is Defender for Cloud Apps?
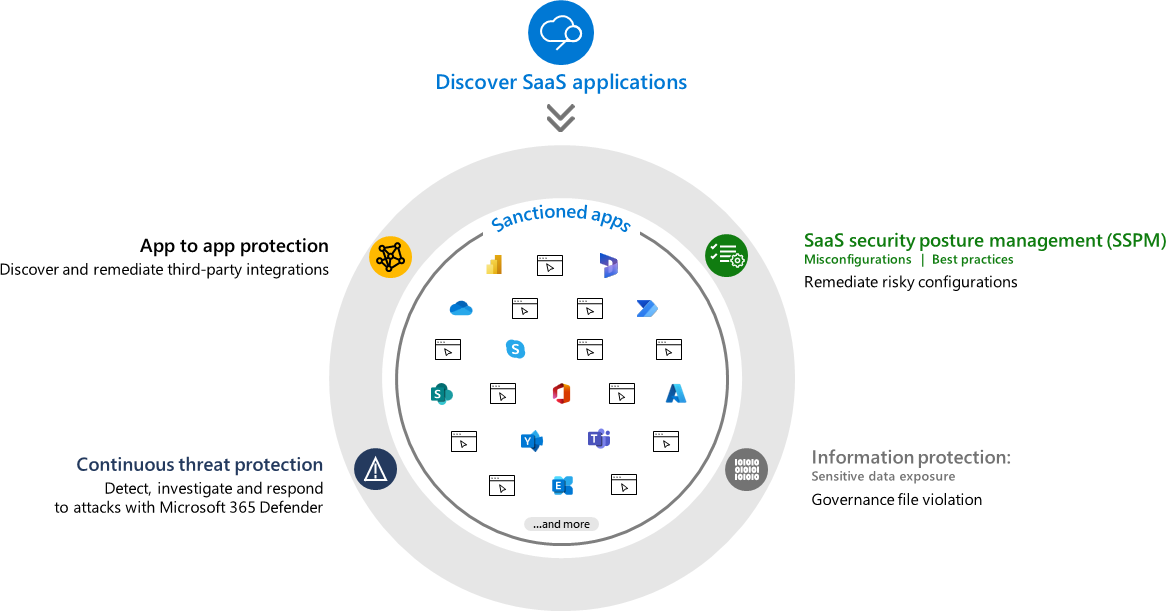
Defender for Cloud Apps aims to tackle the security problems that come with the increasing use of SaaS applications in an organization. Users can quickly and easily start to use a SaaS application even in a way that they consent to it with their work credentials (if your app consent processes are in the default mode). It is therefore increasingly important to see and manage where your users do/can upload your data to. It provides you with the following functionalities:
- Cloud Access Security Broker (CASB) (This is included in the basic Defender for Business and E3 or Defender for Endpoint Plan 1 licenses)
- Provides Shadow IT discovery, visibility into Cloud App usage and built in information protection and compliance assessments.
- SaaS Security Posture Management (SSPM)
- Advanced threat protection
- This comes as a part of Defender XDR and it combines Defender for Cloud Apps with the rest of the ecosystem
- App-to-app protection
- Extends the core threat scenarios to OAuth-enabled apps in your environment
Prerequisites & Licensing
This is one of those cool things that you see on a Microsoft presentation and at the end you get slammed with, “You need an E5 to have this”. Well almost…
I wrote this because this is something that is not fully included in Defender for Endpoint with Plan 2 (included in Microsoft 365 E5 for Security or off course full E5) or Defender for Business (included in Microsoft 365 Business Premium). Though either of them are required as a prerequisite for the standalone Defender for Cloud Apps license if you don’t have the full E5 or E5 for Security. If you are in a position that you dont have the full Defender for Cloud Apps via some license, the standalone license costs just around 3-4€/month at the time of writing and is worth the investment.
You’ll also need to have the devices onboarded to Defender for Endpoint.
Why does this matter?
The functionality of Defender for Cloud Apps has been around for a while. The way that IT management has been done (at least in environments that I have been exposed to) is that the users can roam pretty freely unless something happens and needs to be blocked or dealt with. There is nothing wrong with this and I think that this is the case in most environments.
However, with the rise of AI and different AI tools becoming available more easily it is really important for organizations to use the AI tools that the company provides. This is to protect the company data from getting used as a learning material for AI’s or LLM’s that are not controlled by the company and altogether making sure that the company data is being used in a way that it should be. No imagine the case that you have invested probably thousands of euros into AI development in your organization but your user still use ChatGPT and you possibly pay the bill for their pro subscriptions. That is just a natural way for the users to behave once they get used to use a tool. It’s really hard to convince them to use another one. You just have to make the case as to why they need to use the tools provided. It has to provide more value, of course, but in the end, the users are working for you and they are using your company data
In the below chapters I´ll use AI as an example but the same principle goes for pretty much anything. If you want to see how to secure your company’s own AI apps and agents, checkout my post about Defender for Cloud: AI Workload protection
Cloud Discovery
Now, the cool part about Defender for Cloud Apps in my opinion is the Cloud Discovers functionality. This is where you can get a glimpse of the top statistics about your Cloud App or SaaS app usage as seen from the screenshot below.
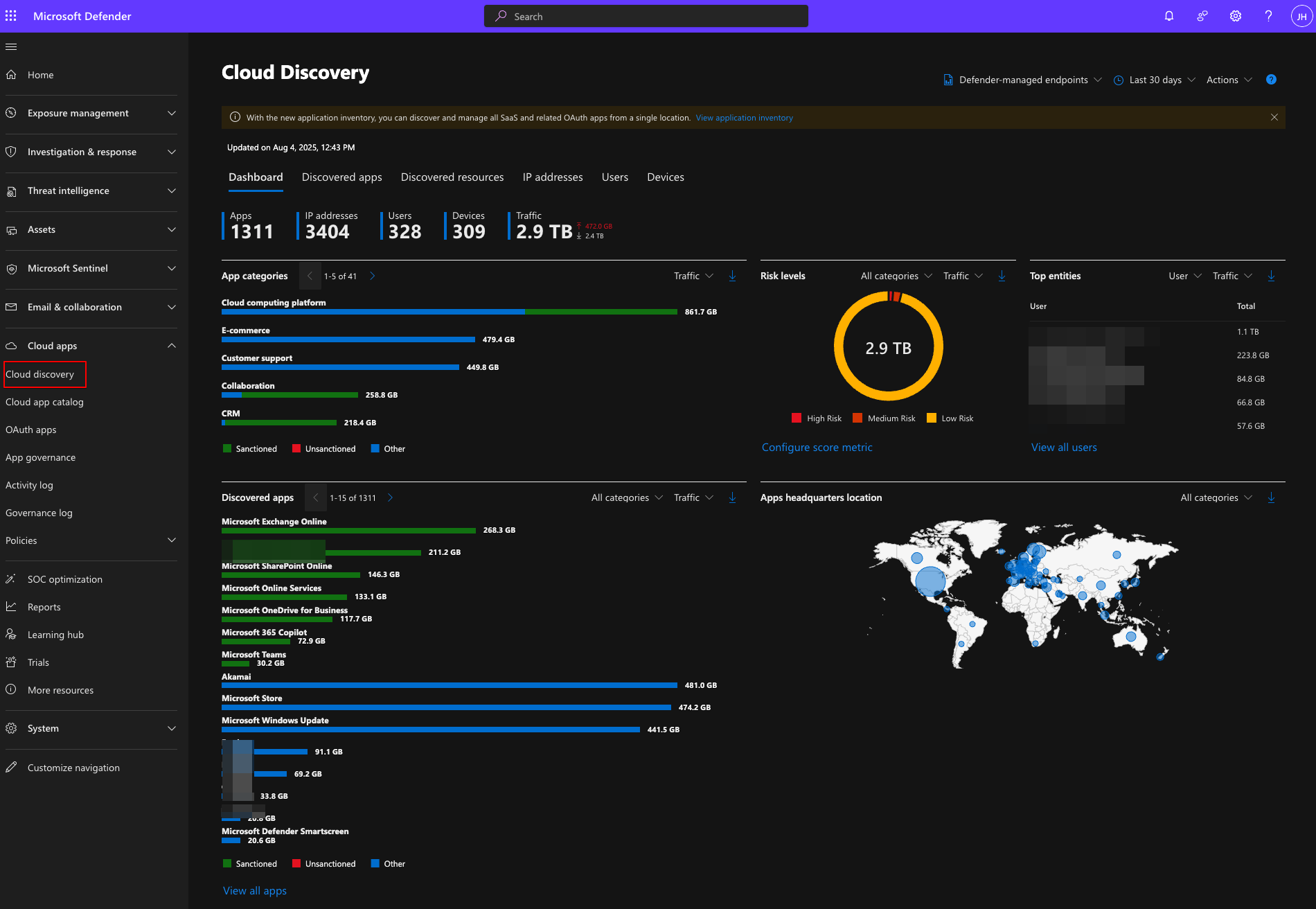
From the Discovered apps tab you can dive deeper into the app usage of your organization for example we can search for AI or generative AI tools and get a list of different AI tools being used with the traffic amounts uploads and downloads, etc. The amount of apps may shock you if this is the first time that you open this portal but this does log all of the apps that are being used on Defender for Endpoint enrolled machine.
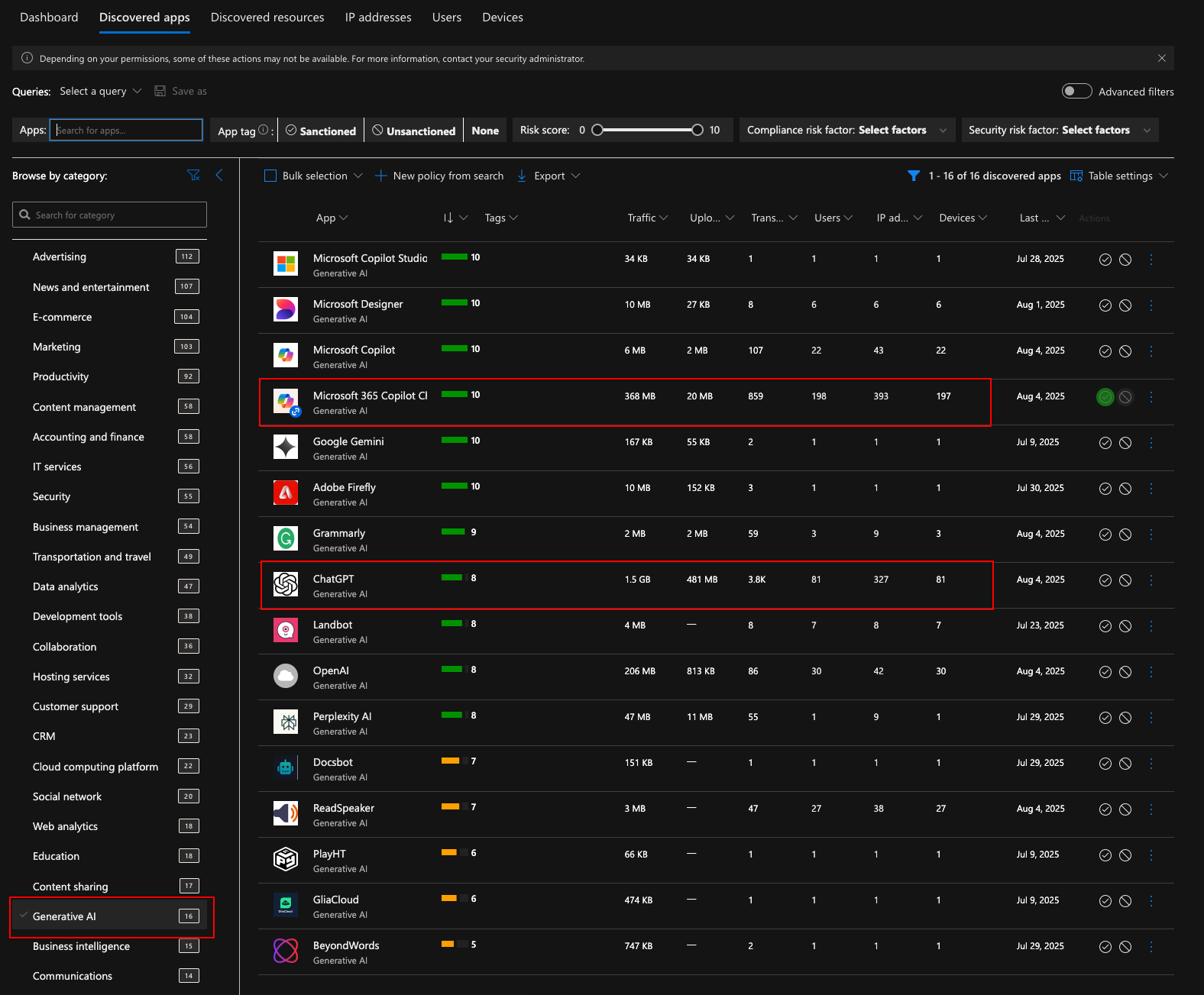
Here we can see a good example of what I talked about at the beginning of this post. You can see that the organization is using Microsoft 365 Copilot but at the same time there’s 1.5 GB of data to ChatGPT and it is used by 81 users. As a security manager, I might wonder what is the data that the users are uploading to ChatGPT and whether there is a case for the organization to build their own GPT using Azure OpenAI, for example.
Now let’s say that the organization owned an OpenAI instance for users. You might want to centralize the usage to an instance that you control so you can provide that with data you own and as a result block ChatGPT. We can also use Defender for Cloud Apps for that, and we’ll get into that in a later chapter about Defender for Endpoint Integration.
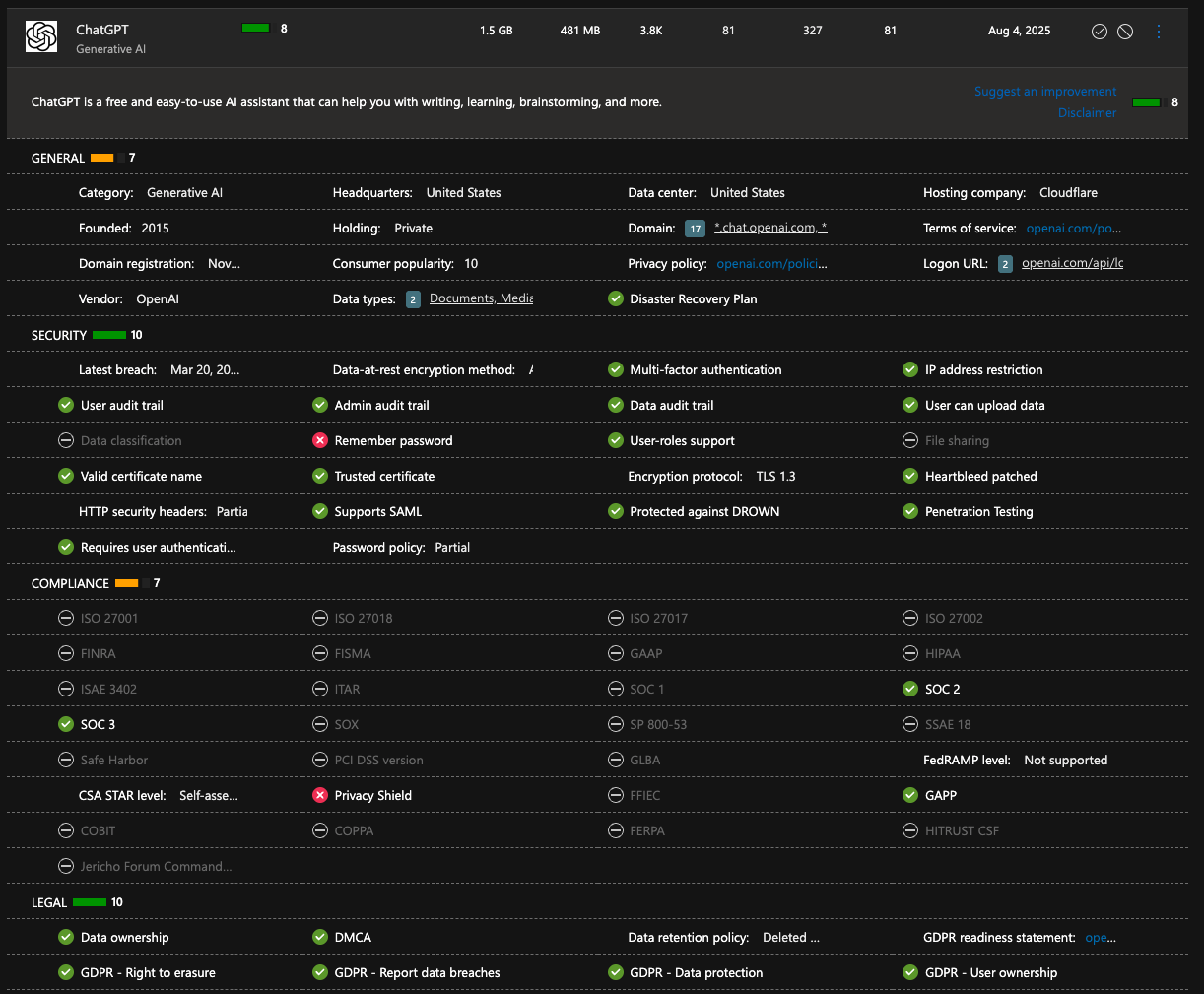
Risk score in Defender for Cloud Apps
You might wonder what are those green and yellow color box and numbers behind them. They are what’s called at risk score score gets calculated from four different categories, they are general security, compliance and legal. Of course the risk score isn’t always correct as cloud ups is depending on publicly available knowledge but it should get you a ballpark figure of the risk and I think that that’s something that absolutely can be used to base some policies on. Below is a breakdown of ChatGPT as you can see it has a risk number of eight and and it has gotten it because it did not pass the checks for remember password and the Privacy Shield.
Policies
A powerful functionality in Defender for Cloud Apps is using the policies. For example, I would not like to allow any generative AI apps that has to risk score of less than six so I could create a app discovery policy, the tags those apps as unsanctioned.
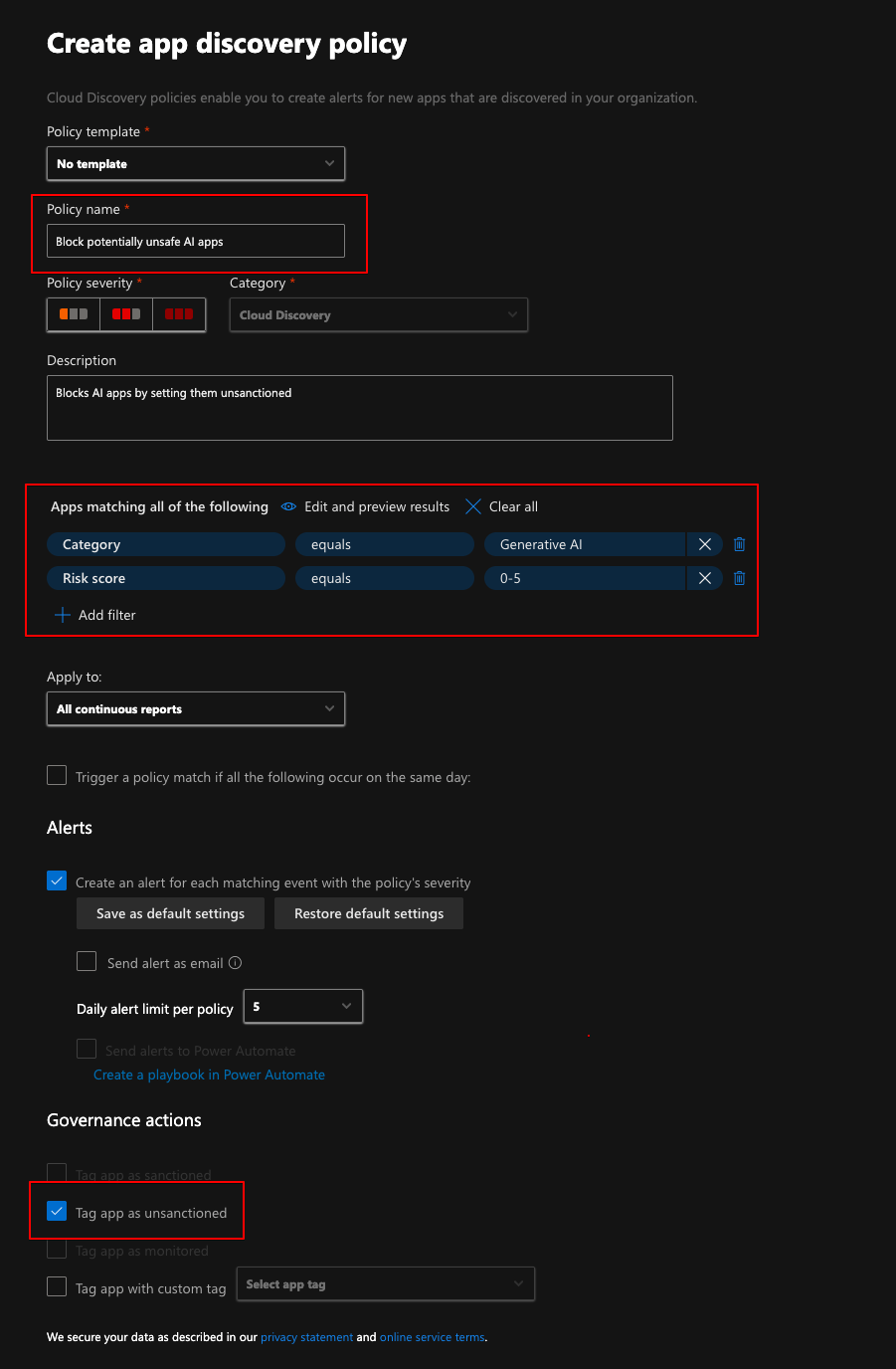
You can do different things like just get notification if a certain type of app is being used or if a new high upload volume app is being detected for example. Just tagging an app isn’t enough, it shows on the reports but doesn’t actually do something and this is where the integration with Defender for Endpoint comes in handy.
Defender for Endpoint Integration
To start with blocking unsanctioned apps, you need to enable the integration from the settings. Navigate to Defender portal -> System -> Settings -> Cloud Apps and under Cloud Discovery, select Microsoft Defender for Endpoint. Notice that after setting “Enforce app access” Defender for Endpoint will block all unsanctioned apps and give a bypassable warning on all apps that are tagged as monitored. It is good practice to make sure you dont have unsanctioned apps when enabling this so you can test and take this into production in a controlled manner.
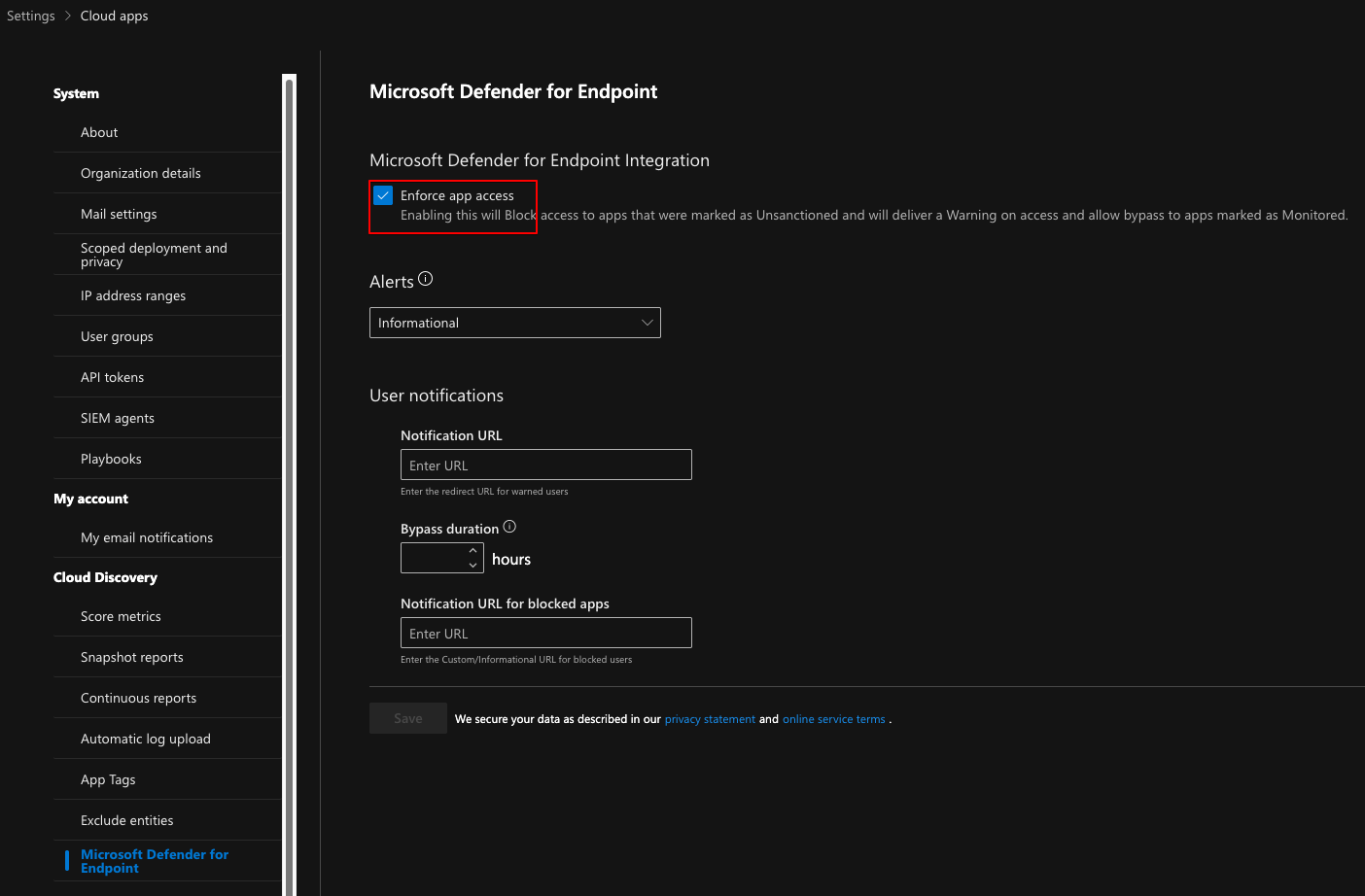
You also need to make sure that the other prerequisites are in order. They are, per Microsoft documentation:
- Defender for Cloud Apps license
- Devices are onboarded to Defender for Endpoint
- Using Windows 10 1709, 1803, 1809 or later (or Windows 11)
- Network protection must be turned on (if on MacOS)
- It is recommended to have the following Defender Antivirus functionalities enabled:
- Real-time network protection
- Cloud-delivered protection
- Network protection configured in block mode
Some discovery data will work without Defender Antivirus but it is highly recommended and you probably have them enabled if you are in Microsoft ecosystem.
Make sure to set the Bypass duration! The settings will not take effect if it is not set and it is blank by default (at least mine didn’t). Also make sure that the Custom Network Indicators are enabled in the Defender XDR settings.
Testing the block (in Monitored mode)
Now for testing purposes I though that my test user cannot use ChatGPT and first tried the monitoring tag. It takes a while for the settings to propagate and the estimate is from 30 min to 3 hours. There might be a lot of variance since my license was just bought vs. someone who has had it for a longer period.
ChatGPT is first set to monitored to see what kind of notification is presented to the user that tries to access it.
And the notification that the user gets below (Native Client):
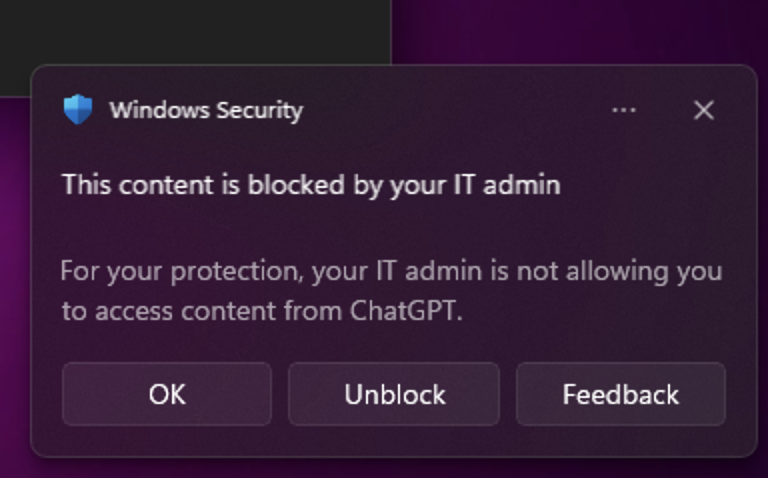
The user can still use the client but the notification keeps popping up unless they click unblock. Browser blocks the access alttogether and gives the following error to the user:
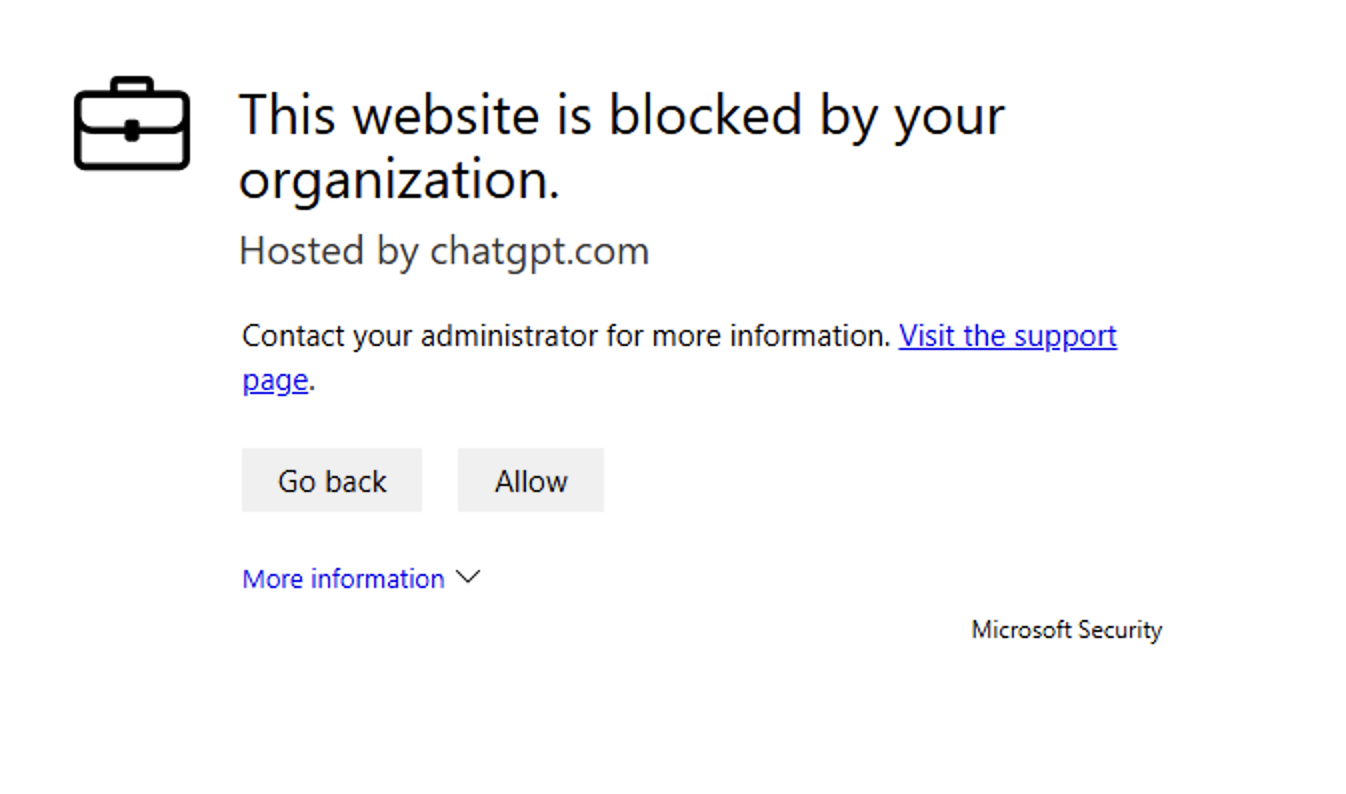
By clicking Allow the user can use it again for the amount of time the admin set in the Bypass duration.
Testing the block (in Unsanctioned mode)
Now let’s try and block the app! There is an option to use Scoped Profiles to apply the unsanction to a certain Device Groups. This might be beneficial in situations where you have a Device Group for Privileged Access Workstations for example and want to block them access to apps they should not use with those devices. I´ll leave it unselected as my test environment has just two machines.
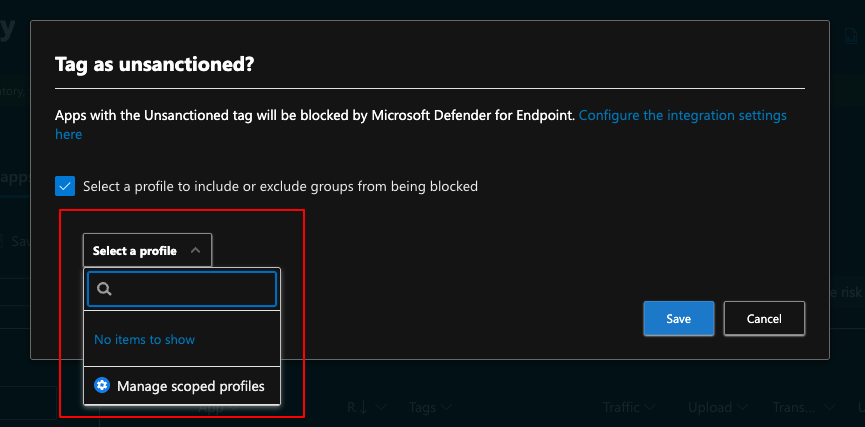
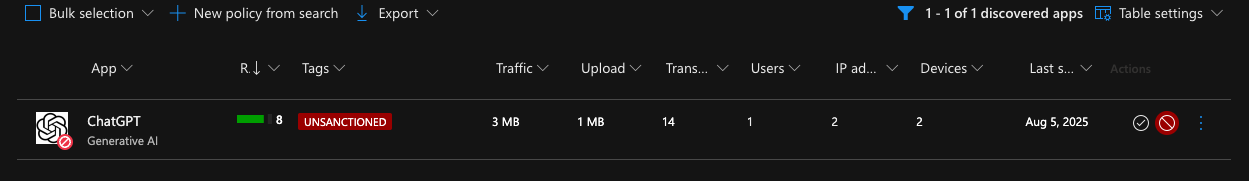
It took some time and at first it felt a bit wonky. I got the blocked notification in the browser (which went away after a refresh) but the native client works perfectly. Its the same notification as in Monitored mode but I dont have the option to allow or bypass.
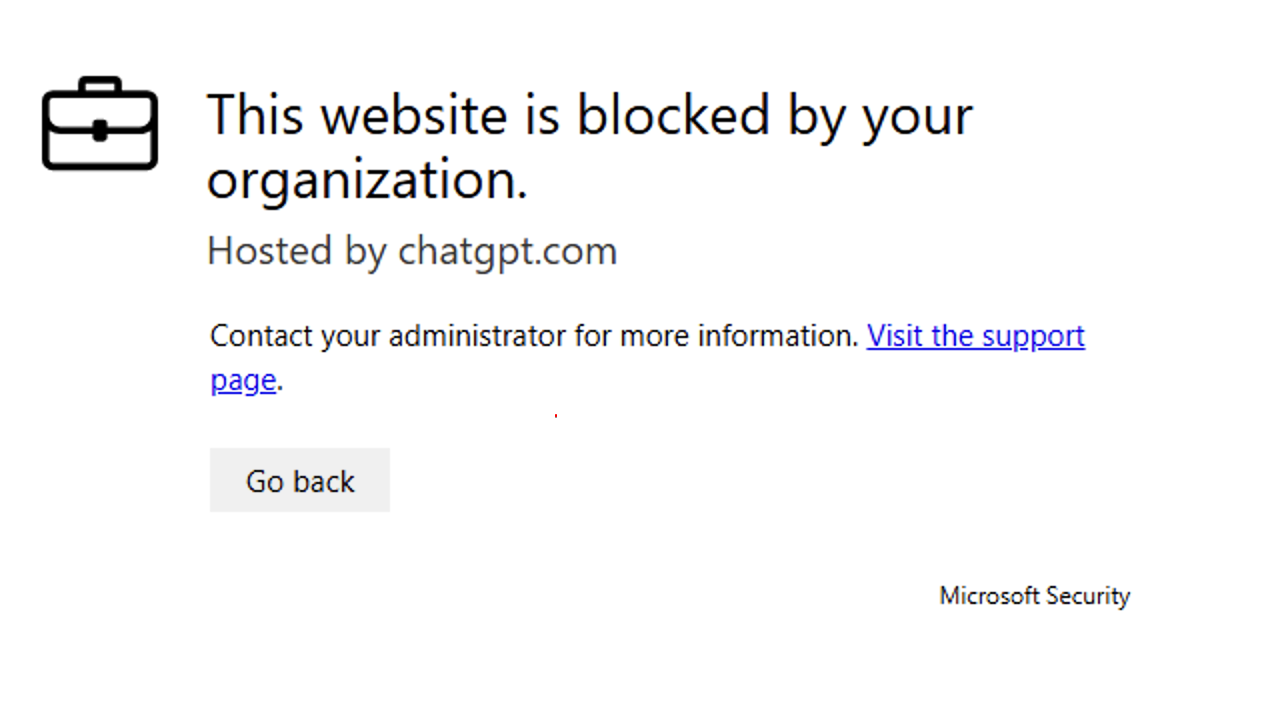
After a bit of waiting (and a reboot) the native client is now blocked as well and I get the following messages:
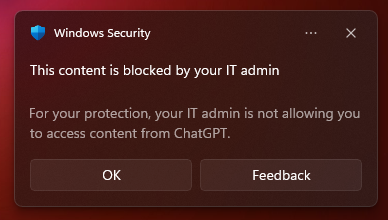
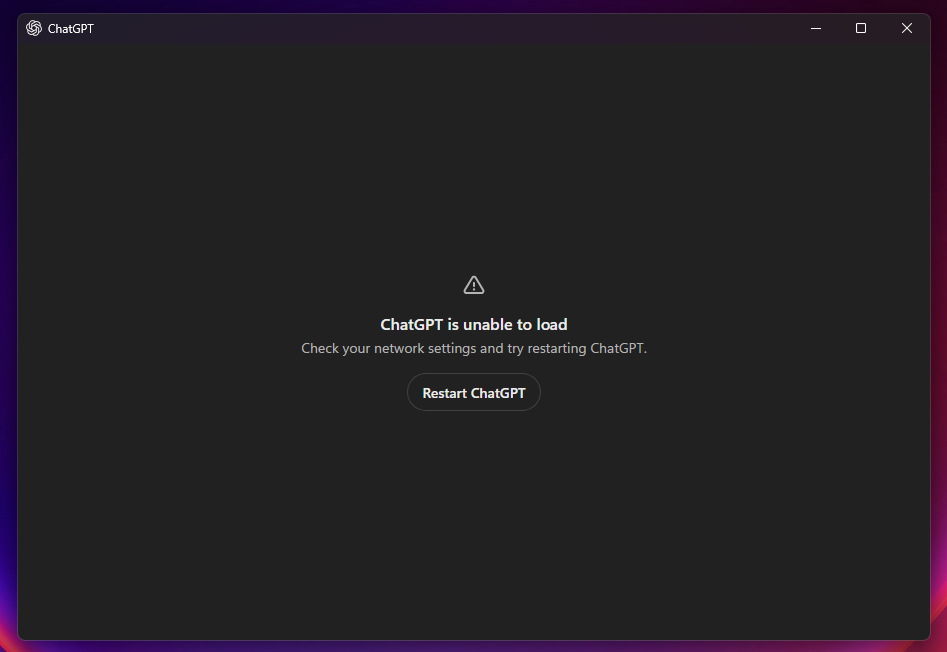
Now this is all well and good and the users cannot use ChatGPT anymore. You could then set a custom redirection to Copilot and guide your users in the right direction.
Detection
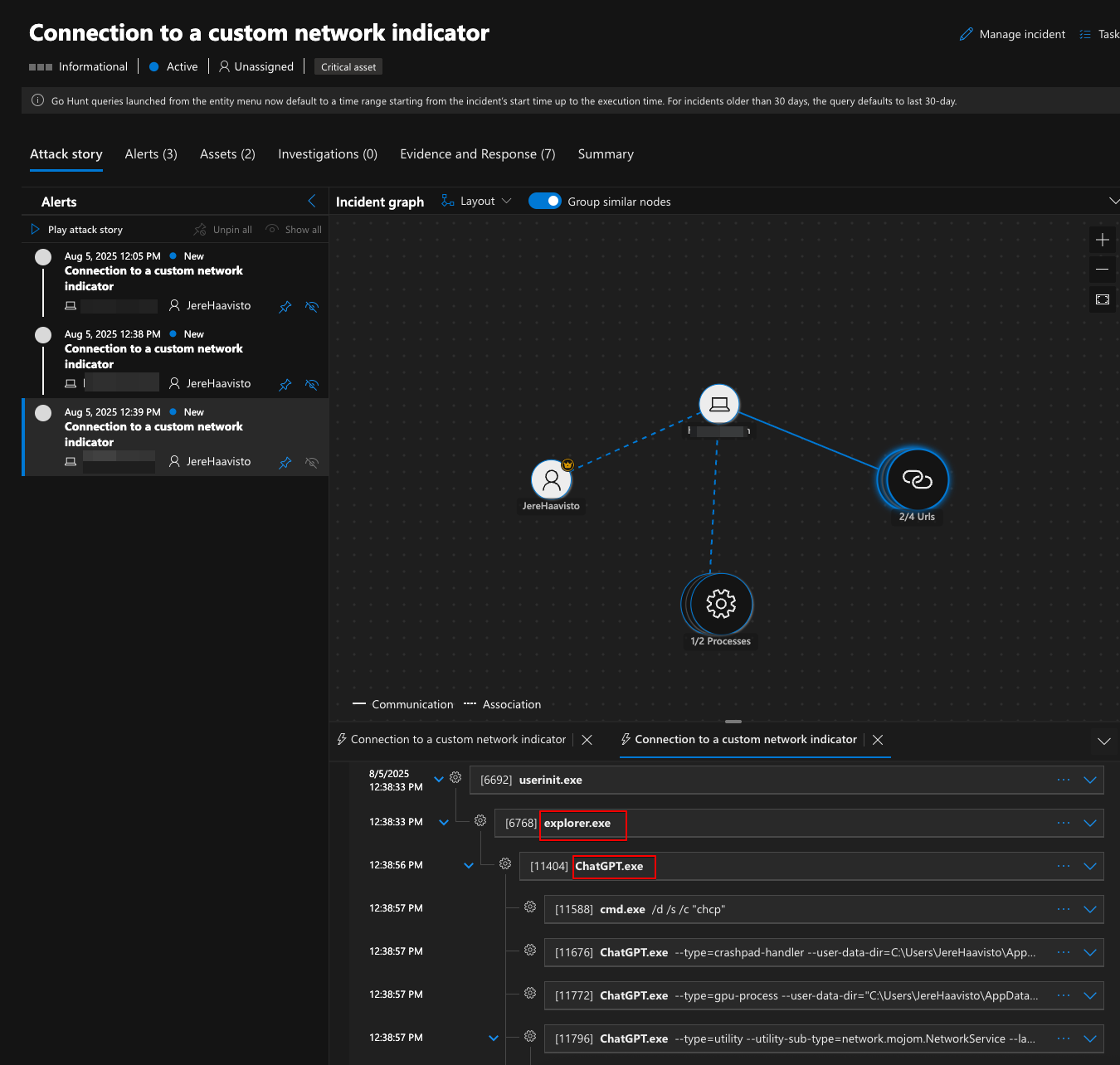
As everyone can probably guess. You get very informative alerts in the XDR portal with the severity you set during the setup that you can also use in Sentinel.
Below is the incident that contains all of the alerts related to my ChatGPT openings. Client first:
And the Browser next:
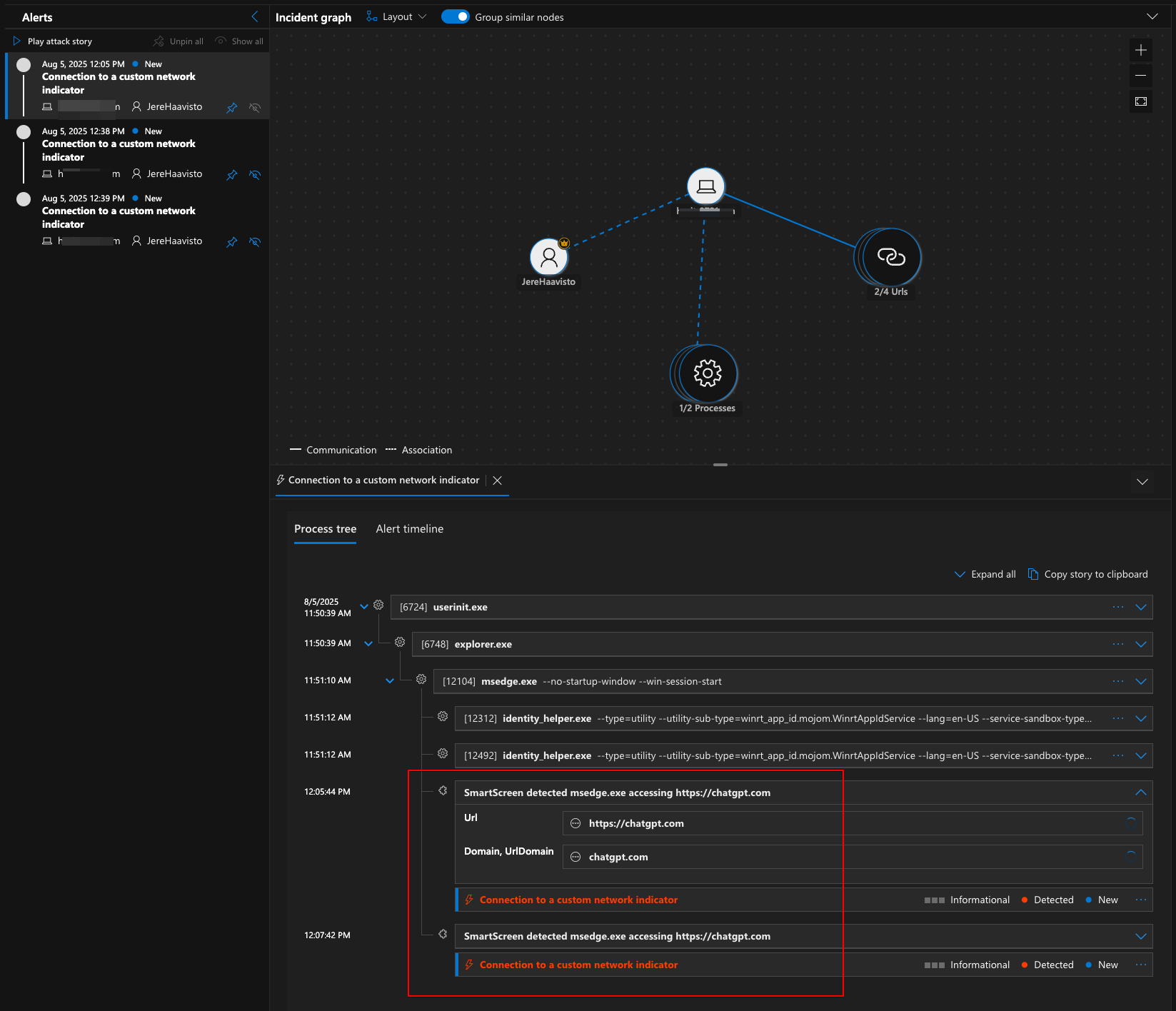
Now you can easily monitor the usage of blocked apps and use that data to educate users of the alternative AI tools you provide them. Don’t get me wrong! I think it is absolutely necessary to use AI tools and I would not just block access to tools before defining which tools to use.
Conclusion
There are a lot of great functionality and tools in Defender for Cloud Apps. This post only scratched the surface with a very specific use-case to demonstrate one functionality. Defender products generally have a lot of functionality that is not used, just because specialists do not have the time to test and familiarize themselves with everything.
Working as a consult gives me the opportunity and privilege to see different environments as well as different ways of doing things. This is really valuable to me because I can really see different solutions to problems.
Leave a Reply